IoT Remote Control Behind Firewall Example: A Comprehensive Guide
In today's interconnected world, IoT remote control behind firewall example has become a crucial topic for both businesses and individuals looking to secure their devices while enabling remote access. The Internet of Things (IoT) has revolutionized how we interact with technology, but it also introduces new security challenges. Understanding how to implement remote control systems securely, especially behind a firewall, is essential for maintaining data integrity and device safety.
As IoT devices continue to proliferate, the demand for secure remote access solutions has increased significantly. Firewalls play a vital role in protecting networks from unauthorized access, but they also create barriers for legitimate remote control activities. This article will explore practical examples and strategies for enabling IoT remote control behind a firewall without compromising security.
This guide aims to provide a detailed overview of IoT remote control systems, including the challenges of implementing them behind firewalls. By the end of this article, you will have a clear understanding of how to configure secure remote access for IoT devices while adhering to best practices in cybersecurity.
Read also:Wave Fest 2024
Table of Contents
- Introduction to IoT Remote Control
- Understanding Firewalls in IoT Systems
- Security Challenges in IoT Remote Control
- Methods for IoT Remote Control Behind Firewall
- Using VPN for Secure IoT Access
- Port Forwarding for Remote IoT Devices
- Cloud-Based Solutions for IoT Remote Control
- Example Scenario: Configuring IoT Remote Control
- Best Practices for Secure IoT Remote Control
- Future Trends in IoT Remote Control
Introduction to IoT Remote Control
IoT remote control refers to the ability to manage and interact with IoT devices from a remote location. This functionality is critical for businesses that rely on IoT systems for monitoring, automation, and data collection. Devices such as smart home appliances, industrial sensors, and security cameras can be controlled remotely, enhancing convenience and efficiency.
However, enabling remote access to IoT devices requires careful consideration of security measures. Firewalls are commonly used to protect networks from external threats, but they can also block legitimate remote control attempts. This section will explore the basics of IoT remote control and why firewalls are necessary in modern IoT systems.
Understanding Firewalls in IoT Systems
A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. In IoT systems, firewalls are essential for protecting devices and networks from unauthorized access and cyberattacks.
Types of Firewalls
- Packet-filtering firewalls
- Stateful inspection firewalls
- Proxy firewalls
- Next-generation firewalls
Each type of firewall serves a specific purpose and offers varying levels of security. Understanding the role of firewalls in IoT systems is crucial for implementing secure remote control solutions.
Security Challenges in IoT Remote Control
Enabling remote access to IoT devices presents several security challenges. Devices connected to the internet are vulnerable to attacks such as hacking, data breaches, and unauthorized access. Firewalls are a critical component of IoT security, but they can also create obstacles for remote control systems.
Common Security Issues
- Unauthorized access to IoT devices
- Data interception and theft
- Denial-of-service (DoS) attacks
- Malware and virus infections
To mitigate these risks, it is essential to implement robust security measures when configuring IoT remote control systems behind firewalls.
Read also:Poppi Louiz Naked
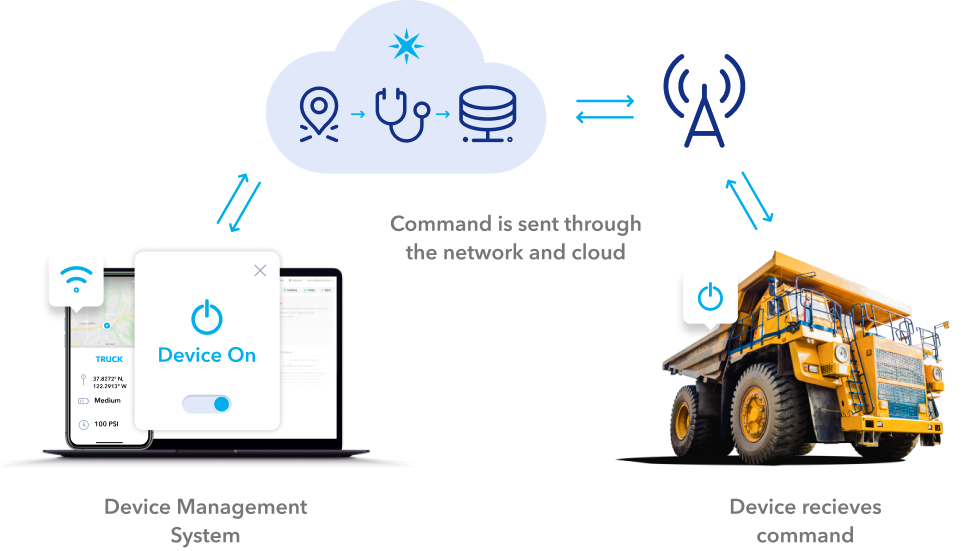
Methods for IoT Remote Control Behind Firewall
There are several methods for enabling IoT remote control behind a firewall. Each method has its advantages and disadvantages, depending on the specific requirements of the IoT system.
Direct Connection
Direct connections involve establishing a direct link between the remote device and the IoT system. This method requires careful configuration of firewall rules to allow incoming and outgoing traffic.
Indirect Connection
Indirect connections use intermediary servers to facilitate communication between the remote device and the IoT system. This approach can enhance security by reducing the need for direct exposure of IoT devices to the internet.
Using VPN for Secure IoT Access
A Virtual Private Network (VPN) is a popular solution for enabling secure IoT remote control behind firewalls. By encrypting data transmitted between the remote device and the IoT system, a VPN ensures that sensitive information remains protected from unauthorized access.
According to a report by Statista, the global VPN market is expected to reach $49.9 billion by 2026, highlighting the growing importance of secure remote access solutions.
Port Forwarding for Remote IoT Devices
Port forwarding is another method for enabling IoT remote control behind firewalls. This technique involves configuring the firewall to forward specific ports to the IoT device, allowing remote access while maintaining network security.
Steps for Configuring Port Forwarding
- Identify the required ports for remote access
- Log in to the firewall or router interface
- Create a port forwarding rule for the IoT device
- Test the connection to ensure proper functionality
While port forwarding is a straightforward solution, it requires careful management to avoid security risks.
Cloud-Based Solutions for IoT Remote Control
Cloud-based solutions offer a scalable and flexible approach to IoT remote control behind firewalls. By leveraging cloud services, businesses can centralize device management and enhance security through advanced encryption and authentication protocols.
Advantages of Cloud-Based Solutions
- Centralized device management
- Enhanced security features
- Scalability and flexibility
- Reduced infrastructure costs
A study by Gartner predicts that cloud-based IoT platforms will account for 70% of all IoT platforms by 2025, underscoring their growing significance in the industry.
Example Scenario: Configuring IoT Remote Control
To illustrate the process of enabling IoT remote control behind a firewall, consider the following example scenario:
Scenario Overview
A small business wants to enable remote access to its IoT security cameras while maintaining network security. The business decides to use a combination of port forwarding and a cloud-based platform to achieve this goal.
Steps for Implementation
- Configure port forwarding rules for the security cameras
- Set up a cloud-based platform for centralized device management
- Implement strong authentication and encryption protocols
- Test the system to ensure secure and reliable remote access
This approach ensures that the business can monitor its security cameras remotely without exposing its network to unnecessary risks.
Best Practices for Secure IoT Remote Control
Implementing secure IoT remote control systems requires adherence to best practices in cybersecurity. Here are some key recommendations:
1. Use Strong Authentication
Implement multi-factor authentication (MFA) to enhance security and reduce the risk of unauthorized access.
2. Encrypt Data Transmission
Use encryption protocols such as TLS or SSL to protect data transmitted between the remote device and the IoT system.
3. Regularly Update Firmware
Keep IoT device firmware up to date to address security vulnerabilities and improve functionality.
4. Monitor Network Traffic
Use intrusion detection systems (IDS) and other monitoring tools to detect and respond to suspicious activity.
Future Trends in IoT Remote Control
The future of IoT remote control is shaped by advancements in technology and evolving security requirements. Some key trends to watch include:
1. Edge Computing
Edge computing enables data processing closer to the source, reducing latency and enhancing security for IoT remote control systems.
2. Artificial Intelligence
AI-powered solutions can improve threat detection and response, making IoT systems more secure and efficient.
3. Blockchain Technology
Blockchain offers a decentralized and secure way to manage IoT device communications, enhancing trust and transparency.
As these trends continue to develop, businesses and individuals must stay informed and adapt their IoT strategies accordingly.
Conclusion
In conclusion, IoT remote control behind firewall example is a critical topic for anyone working with IoT systems. By understanding the security challenges and implementing best practices, you can enable secure remote access to IoT devices without compromising network safety.
We encourage readers to explore the methods and solutions discussed in this article and apply them to their own IoT systems. Feel free to leave comments or questions below, and don't hesitate to share this article with others who may benefit from its insights. For more information on IoT and cybersecurity, check out our other articles on this site.