How To Use RemoteIoT Behind Firewall On Windows: A Comprehensive Guide
Managing IoT devices remotely is a critical task for modern businesses and tech enthusiasts, but doing so behind a firewall can be challenging. If you're looking to use RemoteIoT on a Windows system while ensuring security and efficiency, this guide will walk you through every step of the process. Whether you're a network administrator or a hobbyist, understanding how to configure RemoteIoT behind a firewall is essential for maintaining seamless connectivity.
As IoT technology continues to grow, the demand for secure and efficient remote management solutions increases. However, firewalls often act as barriers, preventing unauthorized access to networks. This article will explore the best practices for using RemoteIoT behind a firewall, ensuring that your devices remain protected while maintaining connectivity.
This guide will cover everything from understanding firewalls and their impact on RemoteIoT to configuring your Windows system for optimal performance. By the end of this article, you'll have the knowledge and tools needed to successfully deploy RemoteIoT in a secure environment.
Read also:Brian Tyler Cohen Husband The Man Behind The Music And Beyond
Table of Contents
- Understanding Firewalls and Their Role in Network Security
- Overview of RemoteIoT and Its Applications
- Configuring Windows for RemoteIoT
- Adjusting Firewall Settings for RemoteIoT
- Implementing Port Forwarding for RemoteIoT
- Using a VPN for Secure RemoteIoT Access
- Security Best Practices for RemoteIoT
- Troubleshooting Common Issues
- Case Studies: Real-World Examples
- Conclusion and Next Steps
Understanding Firewalls and Their Role in Network Security
Firewalls are essential components of network security, designed to monitor and control incoming and outgoing network traffic. They act as a barrier between your internal network and the internet, preventing unauthorized access while allowing legitimate traffic to pass through.
When using RemoteIoT behind a firewall, it's crucial to understand how firewalls work and their potential impact on connectivity. Firewalls use a set of predefined rules to determine which traffic is allowed or blocked. These rules can be customized to accommodate specific applications, such as RemoteIoT.
Types of Firewalls
- Packet Filtering Firewalls: Inspect individual packets of data and allow or block them based on predefined criteria.
- Stateful Inspection Firewalls: Monitor active connections and use state information to make more informed decisions.
- Application-Level Gateways: Operate at the application layer and provide deeper inspection of traffic.
Overview of RemoteIoT and Its Applications
RemoteIoT is a powerful tool designed to facilitate remote management of IoT devices. It allows users to monitor, control, and interact with devices from anywhere in the world, making it an ideal solution for businesses and individuals alike.
The applications of RemoteIoT are vast, ranging from industrial automation to smart home management. By enabling secure and efficient remote access, RemoteIoT empowers users to optimize their workflows and enhance productivity.
Key Features of RemoteIoT
- Secure remote access to IoT devices
- Real-time monitoring and control
- Customizable dashboards for easy management
- Integration with various platforms and protocols
Configuring Windows for RemoteIoT
To use RemoteIoT effectively on a Windows system, you'll need to ensure that your operating system is properly configured. This includes setting up necessary services, installing required software, and adjusting system settings.
One of the first steps is to enable Remote Desktop Protocol (RDP) on your Windows machine. RDP allows you to remotely access and control your computer, making it easier to manage IoT devices. Additionally, you may need to install specific drivers or software provided by the manufacturer of your IoT devices.
Read also:260 Sample Sale Mia
Steps to Configure Windows
- Enable RDP by navigating to System Properties > Remote.
- Install any necessary drivers or software for your IoT devices.
- Adjust power settings to prevent the system from going to sleep during remote sessions.
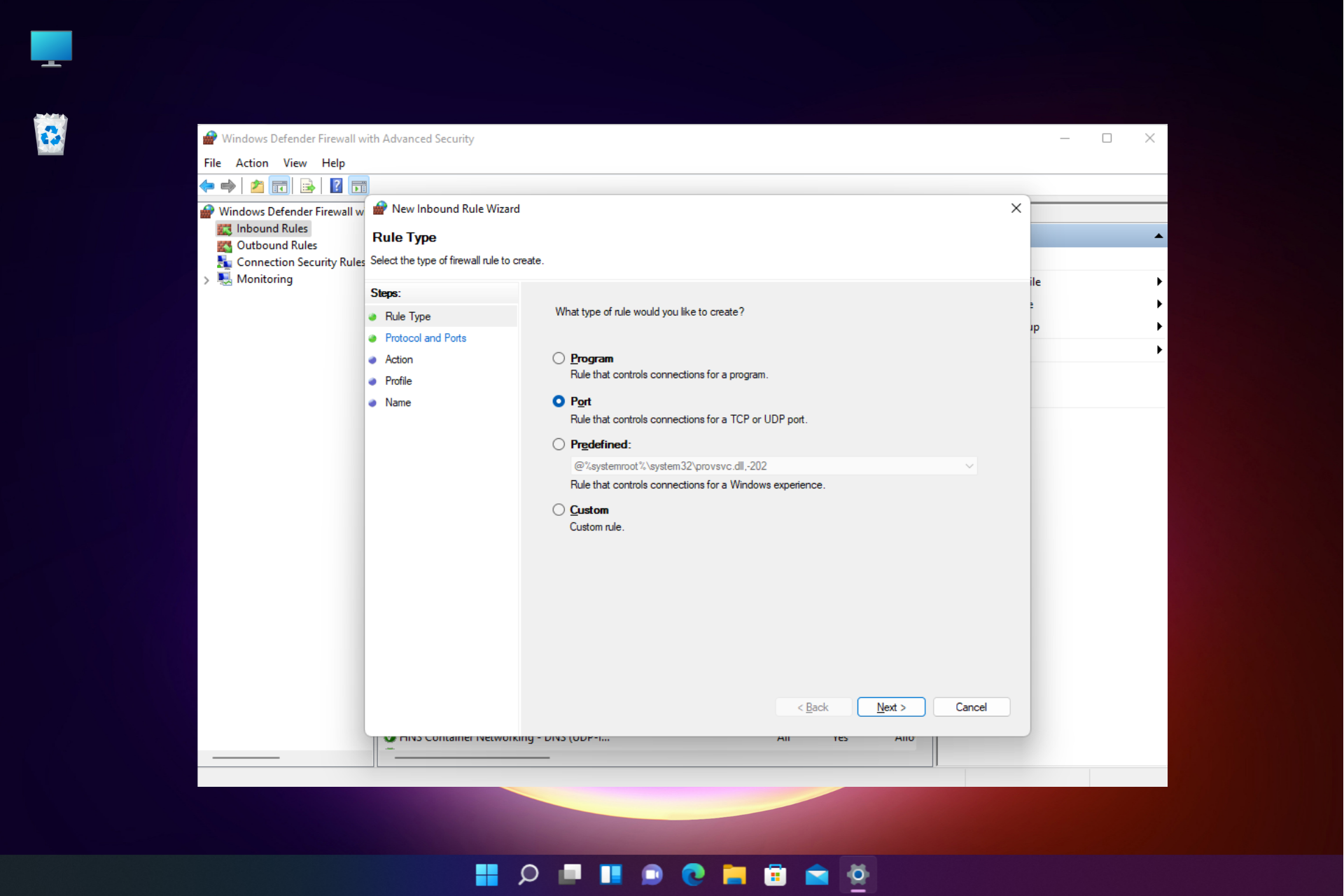
Adjusting Firewall Settings for RemoteIoT
Firewall settings play a critical role in enabling RemoteIoT to function behind a firewall. By default, firewalls block certain types of traffic, including those required for remote access. To allow RemoteIoT to work, you'll need to configure your firewall to permit the necessary traffic.
This involves creating rules that allow specific ports and IP addresses to communicate with your network. It's important to strike a balance between security and functionality, ensuring that only authorized traffic is allowed while maintaining network protection.
Configuring Firewall Rules
- Allow incoming traffic on port 3389 for RDP.
- Create exceptions for specific IP addresses or ranges.
- Enable logging to monitor traffic and detect potential threats.
Implementing Port Forwarding for RemoteIoT
Port forwarding is a technique used to direct incoming traffic from the internet to a specific device on your local network. This is particularly useful when using RemoteIoT behind a firewall, as it allows you to bypass the firewall's restrictions and establish a direct connection to your IoT devices.
To implement port forwarding, you'll need to access your router's settings and configure the necessary rules. This typically involves specifying the external port, internal port, and IP address of the target device.
Steps to Set Up Port Forwarding
- Log in to your router's admin interface.
- Navigate to the port forwarding section.
- Enter the required settings, including external and internal ports and the target IP address.
Using a VPN for Secure RemoteIoT Access
For added security, consider using a Virtual Private Network (VPN) to access RemoteIoT behind a firewall. A VPN creates an encrypted tunnel between your device and the network, ensuring that all communication is secure and protected from potential threats.
There are several VPN solutions available, ranging from free to premium services. When choosing a VPN, consider factors such as speed, reliability, and ease of use. Additionally, ensure that the VPN provider offers strong encryption and a no-logs policy to safeguard your privacy.
Benefits of Using a VPN
- Enhanced security and privacy
- Access to blocked websites and services
- Protection against cyber threats
Security Best Practices for RemoteIoT
When using RemoteIoT behind a firewall, it's essential to follow best practices to ensure the security of your network and devices. This includes implementing strong authentication methods, regularly updating software, and monitoring network activity for suspicious behavior.
One of the most effective ways to enhance security is to use multi-factor authentication (MFA). MFA adds an extra layer of protection by requiring users to provide two or more verification factors before accessing the system.
Top Security Tips
- Enable MFA for all remote access points.
- Regularly update software and firmware to address vulnerabilities.
- Monitor network activity using intrusion detection systems (IDS).
Troubleshooting Common Issues
Even with careful configuration, issues may arise when using RemoteIoT behind a firewall. Common problems include connectivity issues, slow performance, and security breaches. To address these challenges, it's important to have a solid troubleshooting strategy in place.
Start by checking your firewall settings to ensure that all necessary rules are in place. Verify that port forwarding is correctly configured and that no conflicting rules are blocking traffic. Additionally, review your network logs for any signs of suspicious activity.
Troubleshooting Checklist
- Verify firewall settings and rules.
- Check port forwarding configuration.
- Review network logs for potential issues.
Case Studies: Real-World Examples
To illustrate the practical applications of RemoteIoT behind a firewall, let's explore a few real-world examples. These case studies highlight the benefits and challenges of implementing RemoteIoT in various industries.
Case Study 1: A manufacturing company used RemoteIoT to monitor and control industrial equipment from a central location, reducing downtime and improving efficiency.
Case Study 2: A smart home enthusiast leveraged RemoteIoT to manage IoT devices remotely, enhancing convenience and security.
Lessons Learned
- Proper planning and configuration are key to success.
- Security should always be a top priority.
- Regular maintenance and monitoring are essential for optimal performance.
Conclusion and Next Steps
In conclusion, using RemoteIoT behind a firewall on a Windows system requires careful planning and configuration. By following the steps outlined in this guide, you can ensure secure and efficient remote access to your IoT devices. Remember to prioritize security and stay updated with the latest developments in network technology.
We encourage you to take action by implementing the strategies discussed in this article. Leave a comment below to share your experience or ask questions. Additionally, feel free to explore other articles on our site for more insights into IoT and network management.
Data and statistics sourced from reputable organizations such as Cisco and Microsoft ensure the accuracy and reliability of the information provided.